After a few weeks my eBay-order (with the logical analyzer) arrived and I could finally start with probing the signals between the Atmel and CC1150 on the RFT remote for the Itho ventilation-box. The first challenge I faced was connecting the probes to the right traces on the small RFT board. These traces are so small and the pins of the chips are so tiny that’s it’s impossible to attach the probes directly. Taking a closer look at the board I discovered that almost all traces contain testpads. From what I’ve read these are used during manufacturing to check if the PCB has been assembled correctly. For me these pads looked like a perfect surface to solder some wire onto and attach my probes. But which pads do I need to probe? To determine this I first looked up the datasheet of the CC1150 and found the pins for the SPI-protocol. The pins I will need to probe are: MOSI/MISO/CLK/CS/GDO0 and GND. On the CC1150 they are called: SI/SO/SCLK/CSn/GDO0/GND. Using my multimeter and its continuity testfunction I was able determine the pads that are connected to these pins on the CC1150:
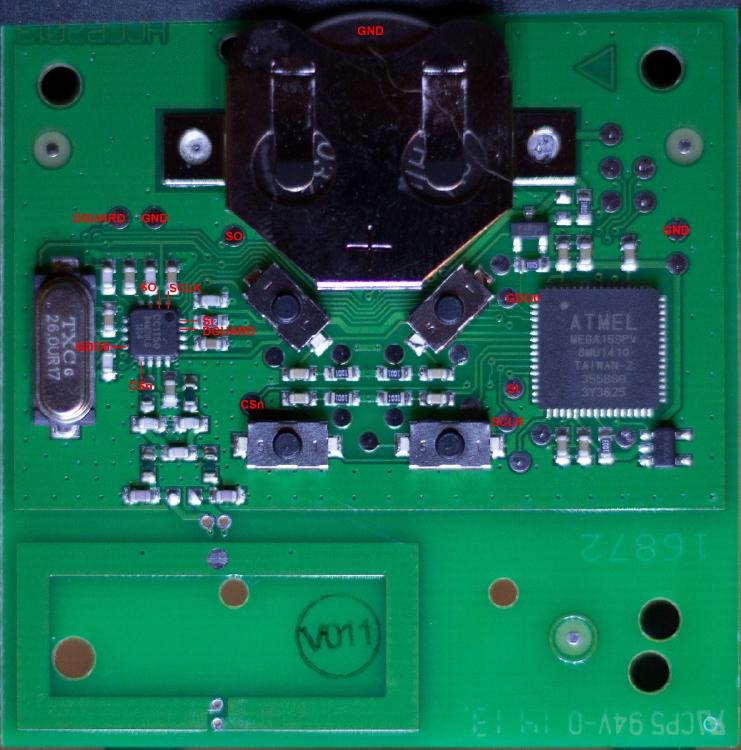
My first attempt to solder some wire onto the testpads succeeded for the first 2 pads, but failed while soldering the third wire. I think I applied to much heat to the pad and damaged the pad (it looks brown and scorched, but solder would not stick). Luckily the remote still worked, but I needed a new plan. Since these are testpads I figured I should be able to create a testbed of some sorts. If I attach a pin to the probe and hold the pin on the testpad the logical analyzer should be able to monitor the signal. Enter all my 3rd-hand tools (you can never have to many helping hands!):


This setup isn’t ideal, because the slightest movement in the arms means the pins don’t touch the pads anymore. It was like playing the game Mikado, think about each movement you make! But it worked! In the logical analyzer appeared a valid stream of data:
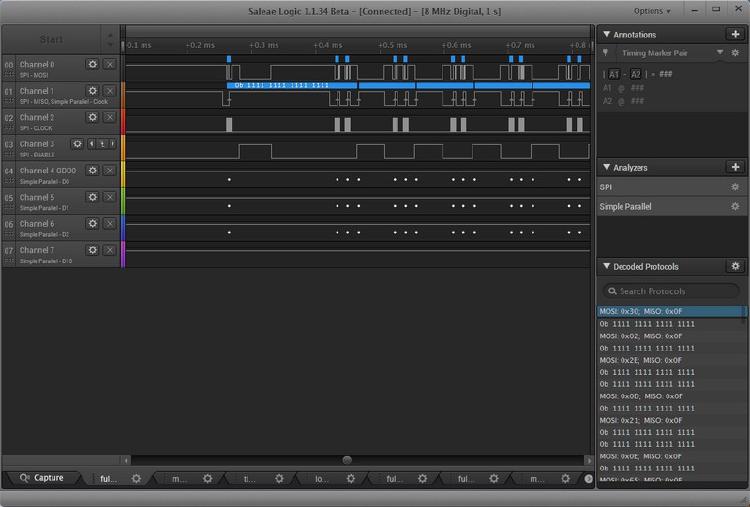
The next step will be to match the probed data with specific commands in the datasheet, to find out what they do and then I should be able to write some code that does the same.
**Other posts in this serie: **Part 1, Part 3, Part 4, part 5, Part 6

3 replies on “Reverse engineering remote Itho CVE ECO RFT - Part 2”
Nice! Patiently awaiting your results..
Nice tinkering! So you want to automate sending the button-commands? You could also use a transistor parallel to the button to simulate a press..?
You are totally right Marc, I could hack the switches on the remote with a transistor. I actually found someone online that did just that. I decided on reverse-enginering because I still want to use the remote afterwards (so I actually want to create an extra remote), and new remotes are expensive (around €70). And this way I’m learning a lot more! :)
Your reply